USB Control and Lockdown Software for Enterprise
USB Management Software for Centralized Device Control and Real-Time USB Protection.
USB Blocking, Whitelisting, Monitoring, and Encryption.
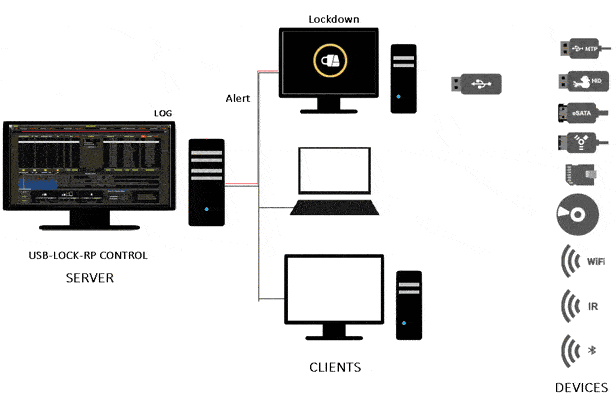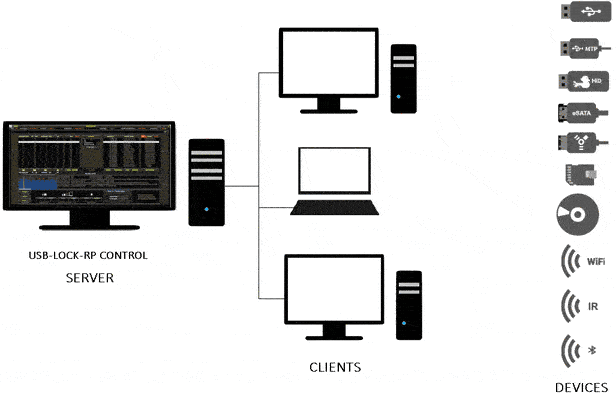
USB Lock RP is robust USB control software designed to centrally manage and restrict access to removable drives, portable devices, and wireless adapters across servers, workstations, and laptops in a network. It features advanced USB Lockdown capabilities designed to block unauthorized USB removable devices and protect computer data in industrial processes and corporate offices.
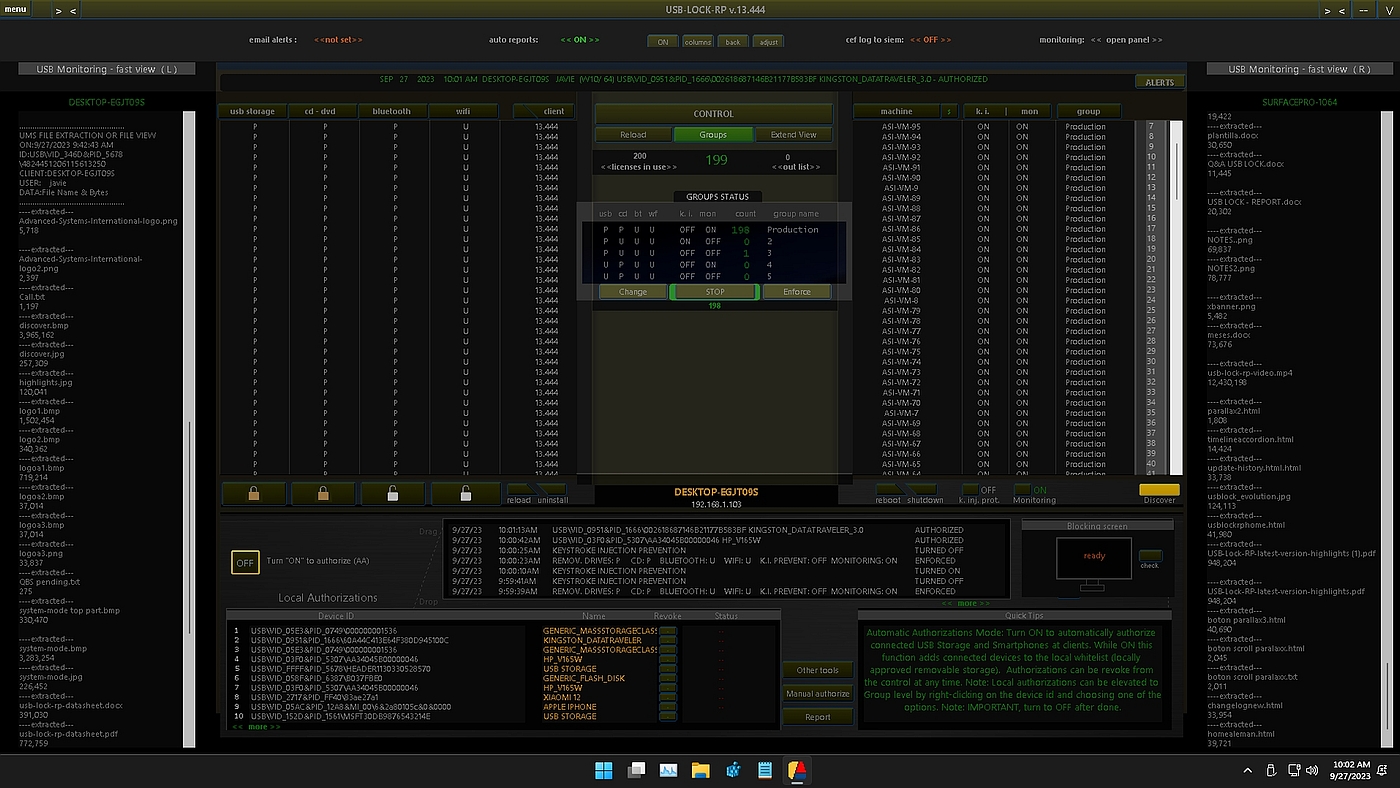
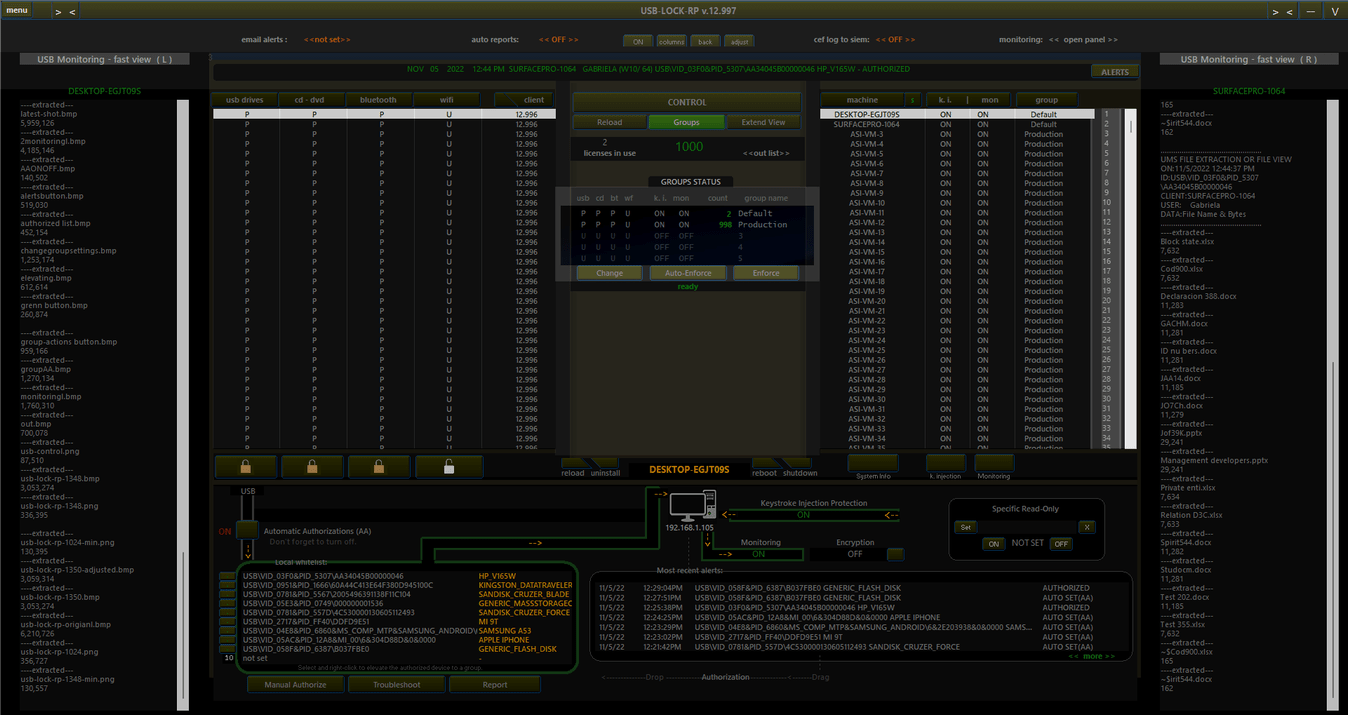
Figure 1: USB Lock RP Control Console(screenshot).
Classified as USB Management and Control Software, USB-Lock-RP is an administrative and security enforcement tool specifically designed to block USB devices and protect data assets on Windows operating systems. It operates independently with a minimal memory and storage footprint.
The Management Console operates on-premises within the enterprise network and provides real-time granular control and visibility over USB activity and endpoint computers. It controls device access policy and enforces rules to specific computers, as well as groups of computers with ease. Receives devices connection alerts and logs events automatically, including USB Monitoring for details on approved file transfers.
USB Lock RP detects devices' hardware IDs to allow specific USB devices and block the rest without interfering with harmless peripherals. USB flash drives can be authorized to work on specific machines, groups or across the network
USB Lockdown is required to effectively prevent data loss and malware infection by means of USB media. USB Lock rejects unauthorized devices at system level and blocks USB incoming and outgoing data.
Its USB blocking and Lockdown characteristics are unique and offer an enterprise-grade USB locker with superior data security than consumer-based USB control solutions or antivirus software attempting to analyze unauthorized devices, because accessing unknown devices creates unnecessary risk and results in a waste of system resources.
Additionally, USB Lock RP provides robust encryption for data transferred from the organization’s computers to authorized USB drives, functioning as a Data Loss Prevention (DLP) measure. This encryption safeguards sensitive information on authorized devices, ensuring that data remains secure not only on the organization’s computers but also while USB devices are in transit. Auto-Encryption can be toggled ON/OFF in real-time, enabling administrators to maintain data security seamlessly as files move between devices and the network.
It is also capable of setting a read-only policy for specific USB drives in real-time. This advanced read-only function write-protects specific USB drives data while other authorized USB drives can be full access on the same machine. (While unauthorized USB drives continue to be blocked)
USB-Lock-RP is advanced USB control software built to block unauthorized USB drives and manage device access with precision. It lets you pre-approve USB devices with ease, log connection events, monitor data transfers, auto-encrypt files to protect data in transit, and more.
USB-Lock-RP integrates easily into existing IT infrastructures, allowing fast deployment across all endpoints with minimal impact. Its lightweight design ensures high performance without hardware upgrades or system slowdown.
Client installation is straightforward and can be done remotely using Windows Installer (MSI) or Group Policy tools, enabling administrators to establish full USB port control across the network quickly and efficiently.
Operating fully on-premises, USB-Lock-RP removes the need for cloud services or internet connectivity, giving you full control over USB device policies and data protection. The Management Console provides centralized administration to apply security settings to individual computers or groups with ease.
Whether securing a small office or a large enterprise, USB-Lock-RP scales to your needs, delivering consistent USB device control and endpoint security throughout your environment.
We are USB Control Specialists — 20 Years of Proven Expertise.
Trusted by infrastructure teams worldwide, USB-Lock-RP is a straightforward security tool resulting from two decades of focused development in USB control.

USB-Lock-RP Device Control is Licensed by Top-notch Organizations Worldwide
USB Control Software for Networks of Any Size
Key Features of USB-Lock-RP Device Control
| Feature | Description |
|---|---|
| Centralized USB Management | Manage and control USB Devices access to USB ports in your network from a single intuitive administrative console. |
| Scalable Network Capability | Proven ability to control USB devices in networks ranging from small businesses to large enterprises. |
| Group and Specific Computer Security | Secure groups of computers or individual machines against unauthorized USB device access, protecting systems and sensitive data across the network. |
| USB Whitelisting | Pre-approve USB devices by hardware ID and block all others. (Four easy ways to pre-authorize specific USB devices in real-time with ease) |
| Real-Time Policy Enforcement | Enforce security policy settings and receive devices connection alerts without delay. |
| Automatic Authorization Mode | Advanced function to Automatically whitelist USB devices on specific machines, and groups of machines in the network. |
| Alerts and Logs | Automatically receive alerts and log USB device connections across the network. |
| Specific USB Port Control | Allows authorization of individual physical USB ports, with selective port exclusion and granular speed control for SuperSpeed (USB 3.x) or High-Speed (USB 2.0) connections. |
| CEF Logs to SIEM function | Enables real-time reporting of security-relevant USB activity to centralized Security Information and Event Management (SIEM) systems. Events are formatted using the industry-standard Common Event Format (CEF), ensuring compatibility with platforms such as Splunk, ArcSight, QRadar, and others. |
| Real-Time Multilingual Device Control | Seamlessly switch between English, French, and German interface languages. View logs, monitor USB activity, and generate reports in your preferred language. Includes multilingual client-side USB blocking alerts to improve communication and support USB device management and compliance. |
| Advanced selective USB Read-Only Setting | Set specific USB drives to read-only while others remain full access, or blocked on the same machine. |
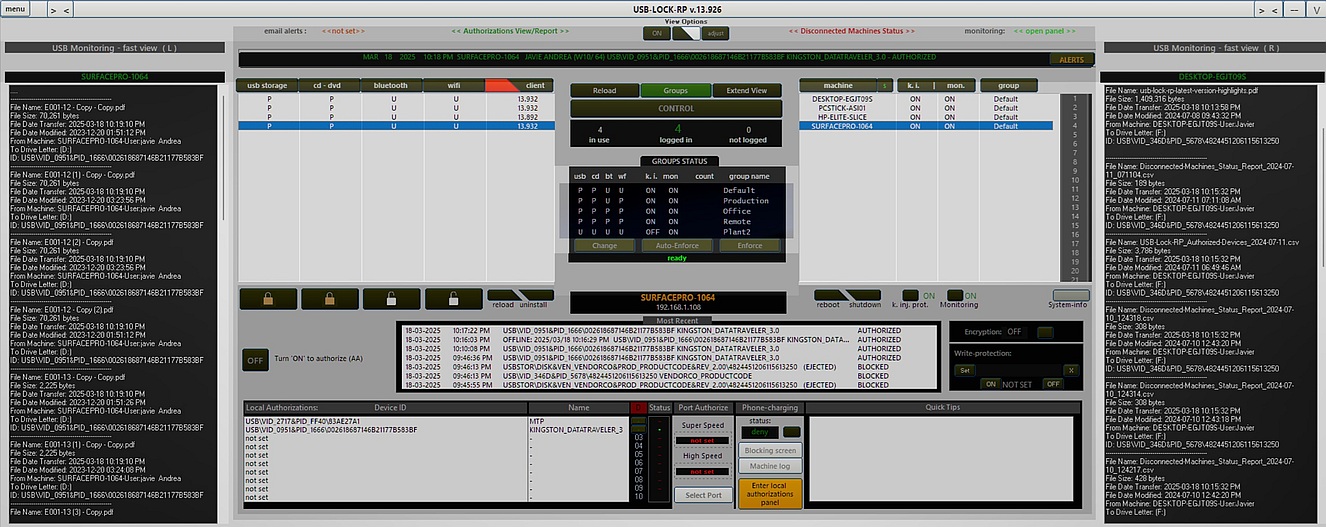
| Enhanced Visibility for Disconnected Machines: | View settings, recent alerts, and authorized devices for machines not currently connected to the network, allowing administrators to efficiently monitor and manage all endpoints. |
| Enhanced Approved Devices Visibility | Displays and exports (CSV) all authorized devices' names and IDs divided by groups, per machine, and group-wide approvals from one place. The new centralized view simplifies the management of USB device authorizations across the network. |
| Remote Desktop Compatibility | Compatible with Remote Desktop; adapts to screen resolution changes and smart desktop area use. |
| Export Reports | Export status and alert reports to CSV format. |
| Full-Screen USB Blocking Alerts | Trigger full-screen alerts when USB devices are blocked, reinforcing USB blocking enforcement with your company logo displayed. |
| Monitor file transfers to USB devices. | USB Monitoring function enables detailed logging of file transfers to USB drives. USB Monitoring logs can also be sent secured to an email inbox within the organization. |
| USB File Transfers Auto-Encryption | USB Auto-Encryption function, When enabled, files copied to USB devices are automatically encrypted using AES-256 and logged per USB session with traceable record IDs. This ensures both visibility and enforcement in secure environments. |
| Easy Client Deployment | Deploy clients easily through Group Policy using Windows Installer MSI. |
| User-Independent Control | Controls USB devices even if no user is logged into the client system (settings and enforcement). |
| Connection-Independent security | Enforces security at client-side even if the client machine is disconnected from the Control. Events while disconnected are received by the Control upon next connection as OFF-Line record. |
Use Cases for USB Lock RP
- Prevent unauthorized USB use in financial institutions
- Enforce USB port lockdown in government or defense systems
- Enable USB encryption for classified file transfers in research labs
Benefits of Using USB Lock RP
| Benefit | Description |
|---|---|
| Data Loss Prevention (USB DLP) | Prevents data loss from computers and from authorized USB devices while in data is in transit. |
| Malware Prevention | Blocks USB devices to prevent malware infections entering computers via USB media. |
| Event Notifications | Informs of USB blocking, approvals, and other device connection events and activities. |
| Regulatory Compliance | Ensures compliance with removable media policies and helps organizations meet data protection regulations and standards such as HIPAA, GDPR, and NIST by enforcing endpoint-level USB control and logging. |
| Perpetual Licensing | Offers a permanent enterprise licensing model with a one-time payment, including two years of updates. Post two years, updates are optional at a reduced cost. |
| Autonomous Control | Designed for autonomous organizational control; doesn't require any external elements or internet connection. |
| Strong Device Control | Blocks or authorizes devices at the endpoint system level in real-time. |
| All-Inclusive Solution | Includes all advanced features — encryption, monitoring, whitelisting, port control, and reporting — with no need to purchase add-on modules. USB-Lock-RP delivers enterprise-grade capabilities that far exceed consumer-grade USB locker tools. |
Software Type:
- Control: USB Management Application (On-Premises, not cloud-based)
- Client: Local System Service
Development Status: Active.
- Latest Version: v.13.932
- Published date: May 23, 2025.
- Dedicated Technical Team on Stand by (Since 2004)
USB Lock RP provides industry-leading USB device control to secure endpoints against unauthorized access. Our advanced USB control software empowers administrators to precisely authorize or block devices, ensuring only trusted USB connections are allowed inside your organization.
USB Lock RP v. 13.926 features the new Light-mode/Dark-mode USB Lockdown and Control Administration Interface: (Image showing the new Light-mode Interface)
USB-Lock-RP serves as an enterprise-grade USB locker solution. Unlike basic USB locking tools, it offers a comprehensive range of advanced features including centralized USB management, real-time monitoring, port-level authorization, file encryption, and more — all tailored to ensure secure USB device control in professional environments.
Real-Time USB Control — Not Just Policy Assignment
USB Lock RP delivers true USB Control by continuously enforcing protection settings and receiving real-time status reports directly from each client machine. Unlike other tools that push policies and assume compliance, USB Lock RP follows a settings-based enforcement model — with Auto-Enforce running constantly to monitor and correct deviations.
You see the actual protection state of every endpoint, grouped or listed individually, exactly as it exists on each machine — no delays, no assumptions. If an exception is needed, you can temporarily disable Auto-Enforce, make adjustments, and instantly restore group settings by toggling it back on.
Even offline clients automatically receive the correct protections the moment they reconnect. This is real-time USB control with full feedback — not just policy broadcasting, but command, confirmation, and continuous enforcement.
USB Control & Enforcement Features
USB Lock RP includes advanced USB control and enforcement capabilities to prevent data leaks, block unauthorized access, and stop malicious USB activity. By ensuring that only trusted and authorized devices are allowed to operate within the network, it helps maintain full compliance and continuous audit visibility — all enforced in real time.
| Feature | Description |
|---|---|
| USB Blocking | Instantly blocks unauthorized USB devices upon connection, preventing data theft and malware injection. |
| USB Whitelisting | Allows only pre-approved USB devices based on unique hardware IDs, giving IT teams granular control over allowed devices. |
| USB Monitoring | Tracks all device connections and file transfers in real time, logging activity for compliance and forensic review. |
| USB Encryption | Encrypts USB file transfers using AES-256 encryption to protect data in transit to authorized removable drives. |
USB Blocking Software
Unlike traditional silent blocking methods, USB Lock RP shows a clear blocking alert directly on the user's screen when unauthorized USB activity is detected at the endpoint. This approach offers real-time visibility and user feedback, enhancing both deterrence and accountability.
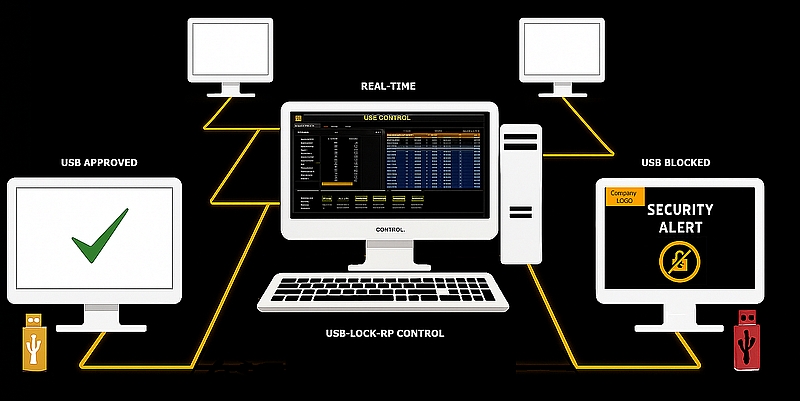
Blocking Alerts vs. Silent Protection
- Personalized blocking screens display the organization’s logo, reinforcing ownership of assets.
- Visible blocking acts as a deterrent — discouraging unauthorized USB connections.
- Easy to audit compared to silent blocking, helping meet compliance and reporting needs.
USB Management Software for Secure Enterprise Environments
USB Lock RP is a dedicated USB management software solution built for organizations that require centralized control over USB usage. It combines real-time enforcement, device-level authorization, per-port restrictions, and enterprise-wide monitoring — all managed from a single, scalable interface.
Administrative Features for USB Management
USB-Lock-RP goes beyond endpoint control by delivering advanced USB management capabilities designed for real-world administrative scale. These features provide enterprise-grade visibility, automation, and operational continuity — ensuring IT teams stay in control without complexity or compromise.
From system-mode persistence to SIEM integration and license resilience, USB Lock RP leads with administrative features that simplify secure USB management across any infrastructure.
| Feature | Description |
|---|---|
| System-Mode Automated USB Management | Runs continuously under the system account to provide 24/7 automated USB device management and real-time settings enforcement — with full administrative control even when no user is logged in. |
| CEF Logs to SIEM | Integrates seamlessly with Security Information and Event Management (SIEM) platforms using Common Event Format for advanced threat monitoring and response. |
| License Recovery | Enables effortless license recovery in case of hardware replacement or OS reinstallation — no re-purchase required. |
| Exportable Reports | Generates USB activity logs in .CSV format for compliance, internal audits, or regulatory reporting. |
USB Whitelisting
USB Authorizations Panel: Provides four easy ways to remotely pre-approve (whitelist) specific USB devices by hardware ID on any machine in real-time:
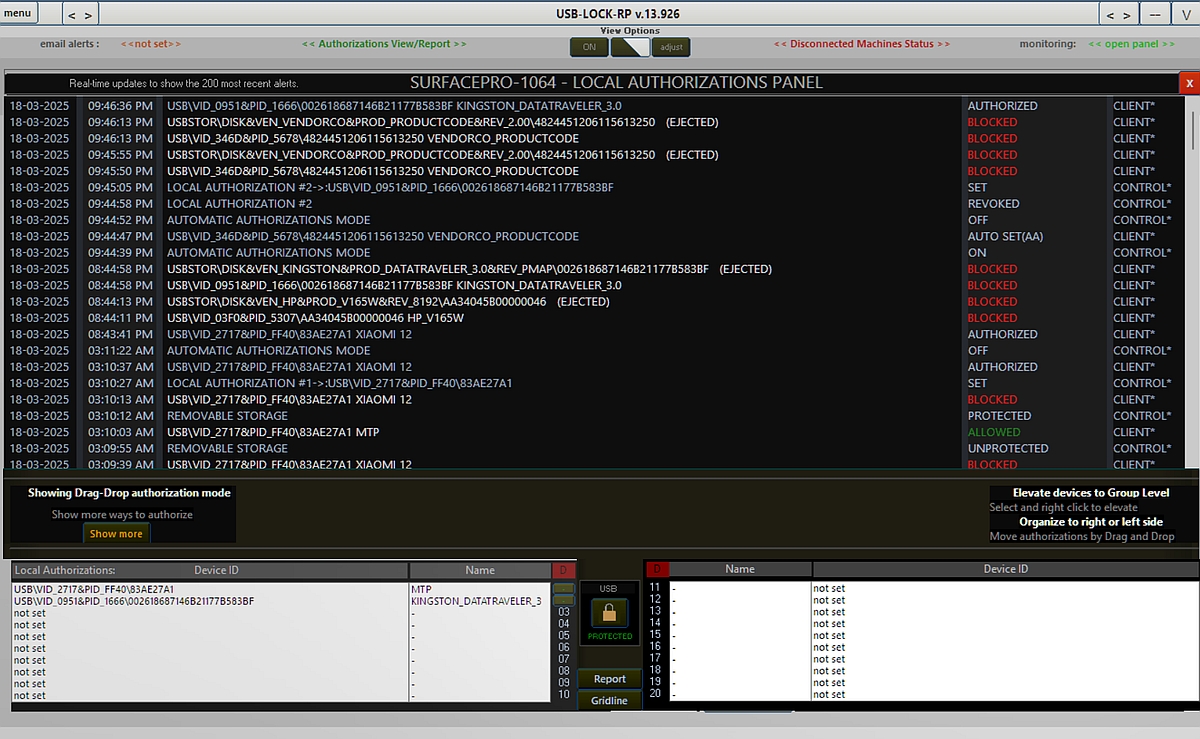
USB Authorization Panel: Provides 4 easy ways to remotely pre-authorize USB devices on any machine in real-time:
| Pre-authorization Method | Description |
|---|---|
| Drag and Drop | Drag from the USB blocked or allowed most recent alerts list and drop into any of the 20 available spots per machine for quick authorization. |
| Automatic authorization | Automatically pre-approve USB devices as they connect to the selected client machine. Can be toggled ON/OFF. |
| Authorize a Connected Device | Pre-approve a USB device that is already connected at the client while the sector is unprotected, allowing immediate access. |
| Manual USB Pre-approval | Manually enter the device ID to authorize specific devices, providing precise control over device access. |
Twenty devices can be pre-approved per machine and a custom name can be included in the record next to the device friendly name for ehanced identification. Authorized devices can be elevated Group level, Group level authorizations can be made to match the Vendor-model or the specific device complete hardware ID, up to 60 specific devices or VID PID match group of devices can be authorized per Group.
USB File Transfer Monitoring
Monitoring the transfer of files to USB drives can be activated or deactivated with just one click independently of the removable storage sector protection state. USB Monitoring can be set to groups or to specific machines. USB Transfer logs are comprehensive and include an auto generated trasfer ID number per USB transfer session, usefull for forensic trasability and when matching to the CEF log transfer details number to ease identifiying the matching transfer records ID number show to SIEM.
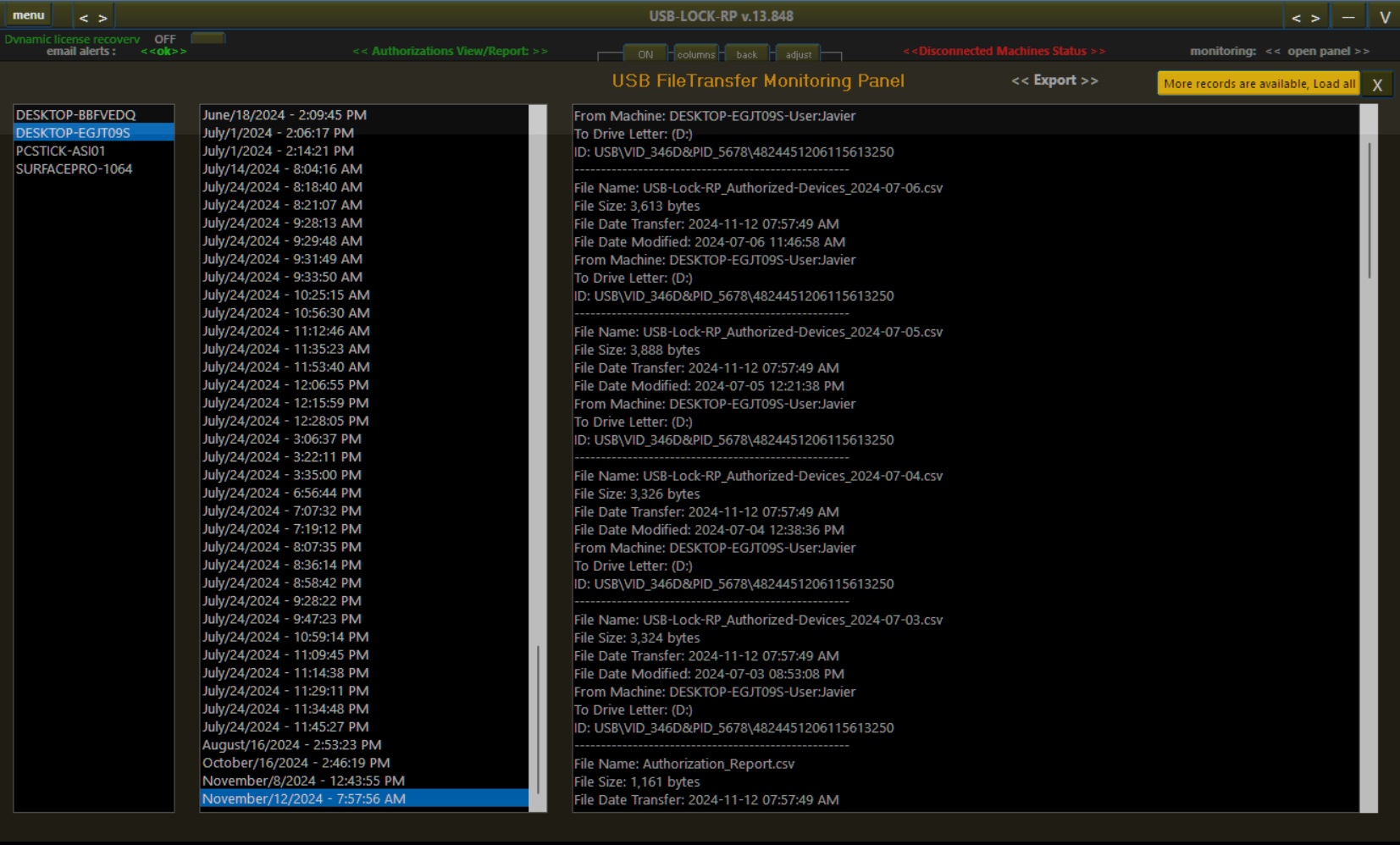
USB File Transfer Logs included:
| Monitored Data | Description |
|---|---|
| File Name | Includes the full name and extension of the transferred file. |
| File Size | Size of the file in bytes. |
| Transfer Date | Date and time when the file transfer occurred. |
| Last Modified Date | Date and time when the file was last modified before transfer. |
| Source Machine Name | Name of the machine from which the file transfer originated. |
| Logged-in User(s) | Name(s) of the user(s) logged into the machine during the file transfer. |
| USB Drive Letter | Drive letter assigned to the destination USB device. |
| Device ID | Complete device ID, including vendor, product, and unique identifiers. |
| Auto-encryption confirmation | If Auto-encryption is set to ON, the record will also includes a AES256 encrypted confirmation for every transfered file succesfully encrypted. (This confirmation is of great value in high security environments) |
File trasfer logs are received by the control in near real-time and are presented for an at a glance view on two side panels and stored in the USB Monitoring Panel organized by machine name/date/time for review when needed.
At the Control server the collected data remains encrypted and same as all device connection alert logs are protected only readable within the control interface.
USB File transfer monitoring logs can be set to be simultaneously sent via secure email to an organization inbox as part of the E-mail alert function if configured. Email Alerts feature secure automatic TLS/SSL Port 587 and TLS/SSL Port Based 465/578, and Supports TLS 1.2
In addition if CEF to SIEM function is set to ON a standarized Common events format log will be generated including the trasfer ID for SIEM reference in case details need to be traced from a SIEM perpective.

- UMS (USB Mass Storage Device).
- USB flash drives.
- Memory Card readers.
- Memory Cards.
- UASP (USB Attached SCSI Protocol).
- Portable Hard drives.
- SSD Enclosures.
- USB-MTP (Media Transfer Protocol).
- Smartphones.
- Tablets.
- Portable devices.
- Smart card readers.
- Smart cards.
- External magnetic hard drives.
- e-SATA.
- Firewire (IEEE 1394).
- Wireless Transceivers.
- WiFi.
- Bluetooth.
- IrDA.
- External and Internal.
- CD.
- DVD.
- Blu-Ray.
- USB-HID (Human Interface Device).
- BadUSBs (Keystroke Injection).
- Arduino.
- USB Rubber Ducky.
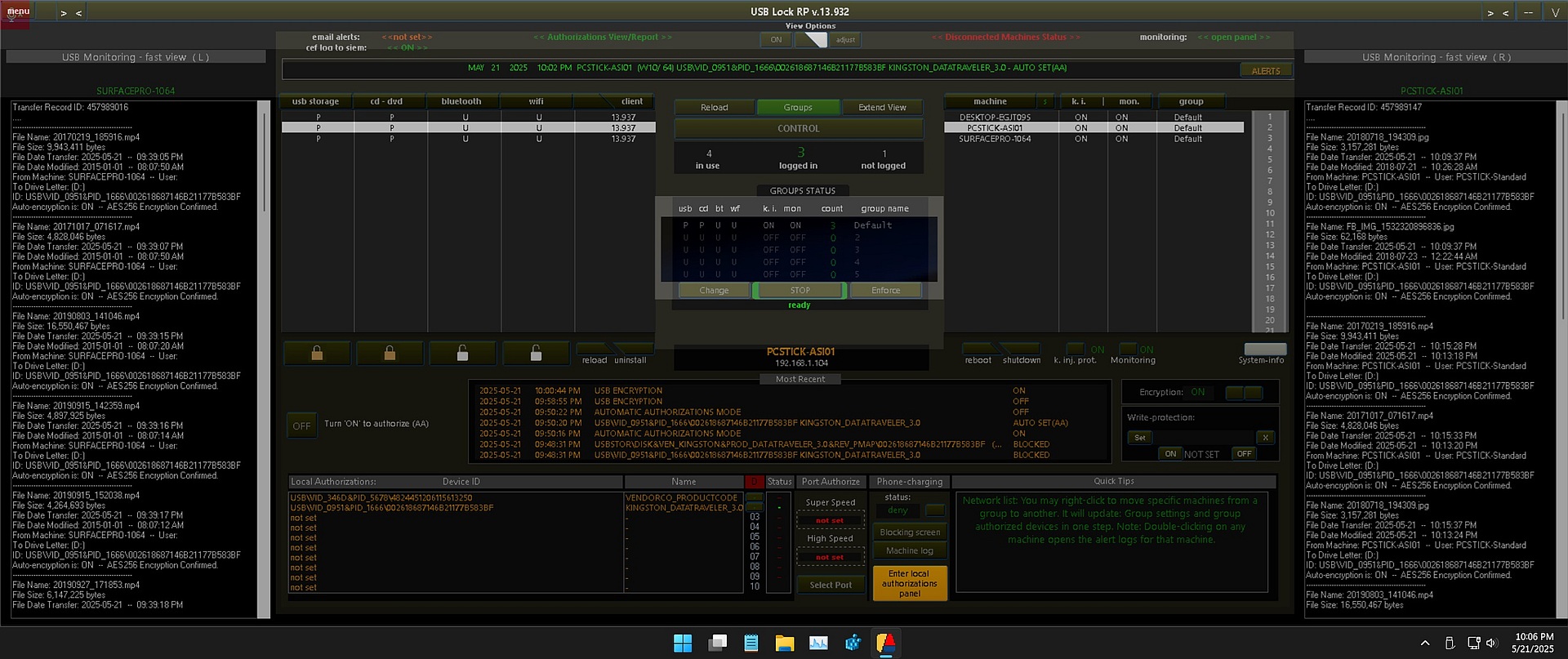
Control USB Devices in Real-time
Strong USB Control:
Prevents zero-day USB-based exploit from entering your systems. Block USB incoming and outgoing of data. Device identifier storage is AES 256 encrypted and HEX masked (variable key and initiation vector in CBC mode). Prevents Hardware ID spoofing. Secures systems even if the user is running with administrative credentials.
Straightforward Operation:
Start protecting your network in minutes. Very easy to operate and set security policy. Protection scope is divided in 4 sectors; just select a client machine or computer group and press the desired lock to keep removable storage and portable devices threats away. Once set operation is automatic. Intuitive administrative GUI, virtually no learning curve involved.
Granular Policy:
Pre-authorize specific USB removable drives and smartphones to access specific computers or all computers in the network while blocking all others. Prevents unauthorized access to USB ports, removable storage, portable devices and other Removable Media from accessing operating systems in the network.
Centralized USB Management:
Centrally set or change security measures and automatically receive and log details on blocked, and authorized USB devices as they are plugged into endpoint computers in real-time. As well as logging and receiving records of files transferred from endpoints to authorized USB Devices as events occur.
Personalized USB Lockdown:
Presents informative Lockdown alerts screens at client computers upon blocking USB devices, USB Lockdown screens presented at endpoint computers are personalized with the end-user organization/enterprise logo. Personalization is automatically done by our team prior to secure electronic delivery (within 3 hours order made)
Smart USB Port Control:
Designed to block usb devices & control USB port access without interfering with non-storage USB peripherals (mouse, keyboards, webcams, printers), But capable of detecting and unobtrusively protect against keystroke injection and malicious payload attacks by devices such as BadUSBs (USB Rubber Ducky) that impersonate HID keyboards or mouse.
USB Monitoring:
Effective monitoring of data transferred from endpoint computers to authorized USB portable storage (thumb/flash/pen drives). Records automatically arrive and are stored secured at the Control server. The Administrative Console can be set to send these records to a SMTP (TLS/SSL) email within your domain in real-time.
USB DLP:
Effective data loss protection USB Lock protects information contained inside authorized thumb drives by optionally forcing automatic AES 256 encryption of all transferred data files from computers to authorized USB drives, effectively locking out USB access to protect confidential information in case the authorized device is lost or stolen. USB DLP policy can be enabled or disabled with just a click.
Perpetual use Licenses:
Licenses are perpetual and include two years of updates, after 2 years updates are optional at 20% of licensing cost. USB-Lock-RP is not support demanding, once it's set, it works as intended, this has to do with product maturity and that at client-side the software deals with hardware, not users. Support is in English at no charge by email or phone.
Autonomous Control:
Doesn’t require internet or Active Directory.
Protects endpoints data even if the client is disconnected from the network. (At the Control, disconnected Laptops will show in the out-list). Protects at System level. (Effective even if running under administrative account.) Starts protecting even if no user is logged into the system. Works on air-gapped networks and remote locations.
Available for Download:
Download the functional DEMO or request a small set licensed as Proof-of-Concept to your organization. Test how USB Lock Software, manages USB ports and devices access to endpoints for free, no cost or commitment. POC Licenses are personalized with your organization logo. Dedicated team on standby to assist on any questions you may have (24x7).
Easy Deployment:
USB Lock client can be easily mass deployed with GPO or any software deployment tool, the USB Lock client is presented as a standalone Windows Installer MSI that is configurable by command line, ensuring effective initial client deployment and updates. Our team can also preconfigure the MSI for you if required at no cost.
USB Lockdown
Refers to automatically blocking access to the computer desktop. Lockdown occurs when unauthorized USB storage devices (e.g., USB 2.0, USB 3.x) are connected to the usb ports (e.g., standard USB type-A, USB type-C), or remote USB. USB-Lock-RP considers the unauthorized connection of usb storage devices a serious intrusion attempt that should be stopped by all means.
USB Lockdown (a.k.a., USB blocking) is part of the software redundant measures applied to protect the system. This measures take place upon USB detection and included preventing drivers to load, stopping, dismounting, disabling, ejecting devices while blocking USB and access to the desktop. Protection measures escalated depending on the device type and the device status but lockdown is normally included when blocking usb and other removable storage under the software protection scope.
USB blocking is a software capability used by IT security administrators to protect computer systems and data assets from threats posed by the connection of unauthorized USB peripherals.
Blocking USB & desktop Lockdown are simultaneous and present full-screen window alerts that extend to multiple monitors.
USB Blocking & Lockdown Remain Active Until Any of the Following Conditions Are Met:
| Condition | Performed At |
|---|---|
| The blocked USB device is removed | Client-side |
| The master password is used | Client-side |
| The sector is unprotected | Control-side |
| The USB device is authorized | Control-side |
Straightforward USB Control
Locking USB Removable Storage Sector on Specific Computers
- Select a client PC from the USB-Lock-RP Control Dashboard network list.
- Click on the left-side lock icon. (removable drives lock)
- Done!, Locking USB only took a second. You have just protected the removable drives sector on the selected computer in real-time.
Now the following devices will be blocked unless specifically authorized: USB removable drive, Mobile phones (MTP Protocol), and memory cards. Setting are enforced in real-time (To unprotect just click the lock again).
Besides Removable Storag Sector, three other sectors to manage are available and are as easy to protect: CD/DVD Sector, iRDA/Bluetooth Sector, and WiFi Sector.
Locking USB Removable Storage Sector on a Groups of Computers
USB-Lock-RP functions as an effective USB locker, enabling you to lock USB ports on entire groups of computers simultaneously. By default, 5 groups are created, and all newly installed clients default to group #1, You're ready to lock USB removable storage and smartphones access across all machines belonging to the group immediately.
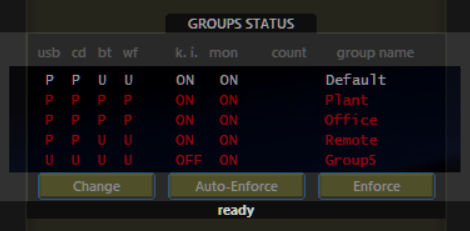
- Press the Change button on the Group Staus Panel
- Select the group name (e.g., Group #1)
- Select the Sector (e.g., Removable drives).
- Select desired action (e.g., Protect)
- Press Save
- Press Enforce
Great!,Locking USB Ports on a Group of computers only took a couple seconds, you just Locked USB removable drives sector on all computers that belong to the chosen group. You will see all computers in that group reporting its security status to protected in real-time.
This group-level USB locking feature makes USB-Lock-RP a powerful enterprise-grade USB locker solution, simplifying protection across your network.
Protection against badUSB devices
Protecting against badUSB device e.g. USB Rubber Ducky is very important. This device type is extremely dangerous, its firmware has been modified to impersonate Human interface devices (HID) such as keyboards.
This class of BadUSB can inflict keystroke injection attacks and introduce malicious payloads to harm the operating system and network infrastructure. Blocking BadUSB is a standard function in USB Lock, the program makes a quick analysis when it detects any change on keyboard or mouse enumeration to prevent such attacks, other than that keyboards and mouse can work normally without restriction.
Specific USB Port Control
Specific USB Port Authorization
This advanced feature provides enhanced control over USB port access by allowing administrators to authorize individual physical USB ports. It introduces flexibility in USB management, usefull in special cases when a USB hub is accessible only to retricted area.
- Selective Port Exclusion: Exclude a specific physical USB port from protection — allowing precise port lock or unlock — while other ports continue enforcing pre-authorization and blocking unauthorized devices.
- Granular Speed Control: Independently authorize SuperSpeed (USB 3.x) or High-Speed (USB 2.0) connections on the same physical port.
Applies to both USB Type-A and USB Type-C connectors.
This USB port control feature helps IT administrators lock or unlock specific USB ports with precision, enabling secure USB port management at the endpoint level.
USB Encryption
The protection of data inside removable storage is done by forcing automatic encryption, this function can also be turned ON or OFF with just one click. (Monitoring needs to be activated for USB encryption to work).
When USB encryption is active all files transferred from the endpoint computer to authorized USB flash drives are automatically AES 256 encrypted. (all data not just the headers)
Stored files on encrypted USB Thumb drives can be opened within the endpoint originating client or within any other endpoint USB-Lock-RP client that has USB Encryption activated. (files are automatically decrypted in those systems when opened)
This function ensures that information contained inside authorized devices is only accessible within determined computers in the network and none outside the network.
Auto-Encryption Security grade (AES256-CBC Mode)
Auto-encryption logic ensures that a unique Initialization Vector (IV) and a primary encryption key are securely derived from the SHA-256 hash of the organization's logo file.
This guarantees:
- Unique encryption per licensed organization.
- Stronger protection against unauthorized decryption attempts, even from other licensed environments.
Note: AES256-CBC Mode encryption is only available to organization within code page 1252 (Windows-1252) system locale.
Reviews:

Reviews For USB Lock Featured at Security Today Buyers Guide (2024):
QUOTE: " USB-LOCK-RP is rocking fast!" Pros: - Easy Interface - Easy Installation via GPO or stand alone - Does not need any extra resources or components to run on any workstations - Runs even on a legacy workstations smoothly - Easy Management Via Admin Control Panel..QUOTE: " Amazing service" Pros: The software does exactly what we need, but it's the responsiveness and quality of support that stands out..QUOTE: " Best for USB/CDRom Blocking" What do you like about USB-Lock-RP? After struggling with fixes, hacks, due to users loading USB and CDRom devices on their workstation adding security risks, I found USB Lock RP 11 years ago. I fell in love with it and been a customer since, continuing to recommend it to anyone trying to secure their network..
Articles:
Auditable USB control
QUOTE: USB control – USB Lockdown blocking screens, which appear at endpoint workstations make it easy for security auditors to test the solution’s effectiveness. With most other solutions on the market, this sort of auditing is not possible.
Auditable USB control, December 18, 2023: USB-Lock-RP,
Article by Francesca Seden in SecurityonScreen.com.
Product showcase: USB-Lock-RP
QUOTE: USB-Lock-RP allows security system administrators to manage USB access from a central administrative console...Preventing unauthorized use of removable media, The solution blocks unauthorized devices as they are connected to computers in the network in real-time.
Product Showcase: February 9, 2021
in: HelpNetSecurity.com
Central Control of Device Access to Computers.
QUOTE: USB-Lock-RP Device Control Software is a unified system to centrally control access to computers by external and remote devices. This protection includes USB ports, removable storage, mobile devices and wireless adapters to servers, workstations and laptops in a network. Specifically, USB-Lock-RP responds to the vulnerability of individual and enterprise-wide computers to cyber exploits...
Article: by Yan Ross
in: CyberDefenseMagazine.com
Direct means of organizations information protection.
QUOTE: ...USB Lock RP is also one of the only pieces of USB control software that personalizes block screens and relevant boxes with a customer’s logo. This builds USB Lock RP into a company’s policy and gives each and every client a feeling of personalized control...
Article: by David Bisson
in: InformationSecurityBuzz.com
Endpoint security that is not a pain in your end!.
QUOTE: ...USB Lock RP not only allows you to maintain control and have flexibility. It gives you peace of mind when it comes to endpoint security and removable devices and more importantly is gets rid of PEST!...
Article: by Ron Barrett
in: NetworkWorld.com