USB Device Control — Controlling, Blocking, and Monitoring USB Devices
USB Device Control is essential to endpoint security. It protects against unauthorized USB access, blocks threats, prevents data loss, and enforces compliance. Controlling USB devices ensures that only authorized ones are permitted, while unauthorized devices are automatically blocked.
Effective device control enforces strict data protection by preventing confidential information from being transferred to USB portable devices. All device activity should be logged, giving administrators full visibility into USB usage and supporting regulatory compliance efforts.
USB ports are often used to connect portable devices such as flash drives, smartphones, and external storage. These devices can be used to transfer sensitive data or deliver malicious payloads.
USB ports support multiple device protocols that enable data storage and transfer. These include MSC, MTP, and UAS, all of which, if left uncontrolled, can be used to extract sensitive data or compromise endpoints.
USB Device Control Is Critical for Enterprise Security
Managing USB Device Protocols for Data Security
Contemporary endpoint systems support numerous classes of removable storage and portable hardware, predominantly interfacing through USB ports using standardized protocols such as MSC, MTP, or UAS. For effective data security and endpoint integrity, it is critical to implement control over the following device categories:
- Removable drives (USB MSC): Flash drives, thumb drives, memory sticks, flash memory cards
- Portable storage (USB MTP/PTP): Smartphones (Android, iPhone), tablets, cameras
- External drives (USB UAS/MSC): HDD/SSD enclosures and high-performance drives
- Optical discs (USB MSC): CD-ROM, CD-R, CD-RW, DVD-ROM, DVD-R, DVD RW, Blu-ray
Note: USB HID (Human Interface Device) connections require special attention to prevent keystroke injection attacks from malicious devices (BadUSBs), while allowing normal use of mice and keyboards.
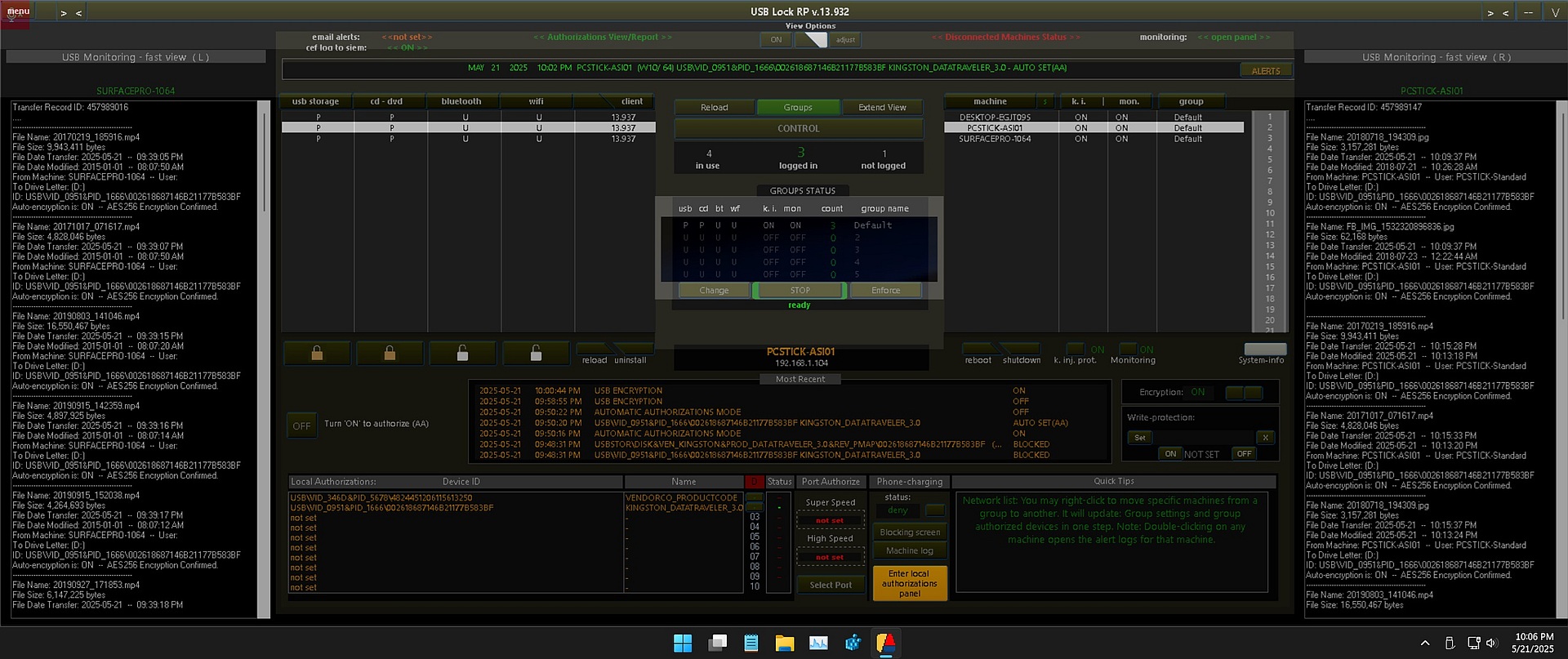
How USB-Lock-RP Enforces USB Device Control
USB-Lock-RP enforces centralized USB device control across the network by blocking unauthorized USBs, approving trusted ones, and monitoring all file transfers with full visibility. It operates entirely on-premises, ensuring total control without cloud dependency, and is trusted by organizations in government, defense, healthcare, and finance.
- Enforced USB Blocking: Prevents unauthorized USB devices from functioning the moment they are connected.
- Device Whitelisting: Authorize USB devices in advance using either their unique serial ID or vendor/product identifier (VID/PID).
- Auto Authorization Mode: Enable automatic authorization for newly connected USB devices on designated endpoints, Automatic approval can be turned ON or OFF.
- Granular Rule Assignment and Enforcement: Apply and enforce USB access settings individually per machine or at group level for efficient management.
- Authorize from Alerts Panel: Instantly permit a blocked device via drag-and-drop from real-time alerts.
- Comprehensive Event Logging: Every connection, approval, or denial is logged to support full audit trails and policy reviews.
Monitor USB File Transfers and Ensure Secure Device Usage
USB-Lock-RP includes built-in USB monitoring to track file transfers to authorized USB storage devices. Each transfer is logged with the filename, size, timestamp, source computer, destination drive, and the destination device's hardware ID—providing complete visibility for auditing and compliance.
For organizations that require it, USB-Lock-RP also includes optional AES-256 encryption for files copied to authorized USB drives. When enabled, encryption is applied automatically per transfer session and logged with a unique record ID to ensure traceability and protect data during transit.
Approving USB Devices
USB-Lock-RP provides multiple authorization methods to ensure only trusted USB devices are allowed. Devices can be approved based on unique hardware identifiers, assigned to specific endpoints or groups, and managed in real-time through the Control Console.
- By Unique Device ID: Allow USB access based on each device’s individual hardware or serial number.
- By Vendor & Product ID (VID/PID): Grant access to known models from trusted vendors using standard USB identifiers.
- Assign per Machine or Group: Apply device permissions to specific endpoints or defined endpoint groups.
- Auto-Approval Option: Enable a mode that automatically authorizes newly connected USB devices when permitted.
- Preload Authorizations: Add trusted device IDs manually in advance for environments requiring proactive control.
- Approve from Alerts: Use drag-and-drop from the alerts panel to instantly authorize devices that were just blocked.
- Revoke Instantly: Cancel device permissions at any time with no delay or restart required.
- Audit-Friendly Reports: Export complete authorization lists per endpoint or group for security audits or inventory reviews.
This straightforward and flexible authorization model is especially valuable in environments such as government, industrial control systems (ICS), defense, and finance—where strict USB access control is essential to operational security.
Other USB Device Control Capabilities Included in USB-Lock-RP
- Specific Physical Port Authorization — Control USB access at the individual port level.
- Auto-Encryption — Secure data in transit by automatically encrypting files copied to authorized USB devices.
- Selective USB Device Write Protection — Set individual authorized USB drives to read-only mode while others remain full access.
- Auto-Enforce Group Policies — Automatically monitor and reapply group security settings to ensure endpoint compliance.
- System Mode — Allows the Control Console to run in the background, silently receiving alerts and enforcing policies 24/7, even when the main admin interface is closed. Ensures uninterrupted USB control and removable media surveillance.
Administrative Management Benefits
- Instant Policy Enforcement: Apply, update, or enforce USB rules in real time — whether targeting individual endpoints or entire groups. Eliminates delays that could leave systems vulnerable.
- Centralized Visibility: The main dashboard gives a clear overview of endpoint device security status, streamlining the shift between broad oversight and detailed control.
- Real-Time Event Capture: USB activity is automatically detected, displayed, and logged. This boosts incident response and simplifies compliance reporting in sensitive environments.
- Encrypted Administrative Logs: Logs containing device and usage data remain protected, accessible only through the USB Control interface or when producing encrypted reports.
- Background Monitoring Mode: The Control Console can operate silently in system mode, maintaining full enforcement and alert reception — even when not actively used.
- Transfer Logging with Encryption Option: Monitor files moved to approved USB drives and optionally encrypt them to safeguard data in case of loss or theft.
Client-Side Protection Highlights
- Customized Full-Screen Blocks: When devices are blocked, a full-screen message displays your company’s logo and a custom note to guide users in requesting approval.
- Lightweight Footprint: The USB-Lock-RP client is optimized for efficiency, consuming virtually no CPU under normal conditions.
- Defense Against Peripheral Threats: Restricts Wi-Fi and Bluetooth transfers and guards against automated keystroke injection attacks without needing to whitelist every peripheral manually.
- Clear Endpoint Control View: Visual indicators help administrators understand USB control behavior during rollout and ongoing management.
Industry Use Cases for USB Device Control
USB-Lock-RP is deployed in high-security and compliance-driven environments worldwide. Here’s how it supports critical operations across industries:
- Government & Defense: Enforce strict USB lockdown policies to prevent data leakage and block unauthorized removable media.
- Healthcare: Protect patient data and maintain HIPAA compliance by controlling device access at every endpoint.
- Finance: Monitor and log file transfers to meet audit requirements and prevent insider threats.
- Manufacturing & SCADA Systems: Prevent tampering by disabling USB ports on industrial control systems, while allowing secure engineering tools.
- Education & Research: Limit access to only approved USB devices in labs and administrative departments.
Trusted USB Device Control
Our USB Device Control software gives you full control over USB access across your organization. You can block unauthorized USB devices, whitelist trusted ones, monitor activity, and even encrypt data — all in real time.
With over 20 years of development, USB-Lock-RP is a trusted solution used by IT security teams around the world. It works entirely on-premises, with no cloud dependencies — ensuring maximum security and complete control.
Whether you manage a few computers or thousands of endpoints, USB-Lock-RP provides superb USB device management that scales with your network. It installs easily using standard tools like Group Policy or MSI packages, and it delivers powerful, centralized USB device control.
Controlling USB Devices in Enterprise Environments
Controlling USB devices is essential to prevent unauthorized data transfers, stop malware propagation, and enforce organizational security policies. USB-Lock-RP provides robust, real-time tools to manage USB access at scale — ensuring devices are either approved, restricted, or blocked based on precise rules.
Below are key features that support effective USB device control across your network:
- Real-Time USB Device Blocking: Instantly block unauthorized USB devices across all connected endpoints.
- Device Whitelisting: Approve specific USB drives or smartphones by unique hardware ID to allow legitimate use.
- Centralized Management Console: Control and monitor all clients from a single interface without delay.
- Detailed Logging: Log every USB connection, including device ID, user, client name, date, and time.
- Read-Only Mode: Allow USB access for reading data without enabling file transfers or write permissions.
- Keystroke Injection Protection: Detect and block BadUSB-style HID attacks from rogue USB devices.
- Remote Device Authorization: Grant temporary or permanent access to USB devices from the control console.
- Encrypted File Transfer Option: Automatically encrypt files moved via USB to ensure data confidentiality.
Get Started with USB Device Control Today
Looking to implement secure and scalable USB device control across your organization? USB-Lock-RP delivers trusted protection without the complexity. Contact us for a live demo or pricing quote.
To learn more and evaluate USB-Lock-RP in your environment:
Download the USB-Lock-RP Demo
Test with 4-client capacity. Immediate access, no registration required.
Request Courtesy Licenses
Receive a personalized, licensed Proof of Concept version (10-client capacity) — ideal for evaluation by organizations and security teams.
